Key Takeaways
- SMB identity security is best anchored in Okta, using MFA, SSO, LCM, and Zero Trust to close the primary attack path.
- Structured implementation prioritizes consolidating and securing digital identities, then locking down email and productivity apps.
- Quantifiable ROI reduces incidents and yields significant productivity gains across users and IT.
- Trusted delivery: Proven IT service providers like NENS can bring a repeatable approach for a reliable, robust security.
Contents
- Why SMB identity security matters—and what IAM is
- The role IAM plays in protecting SMBs
- Getting started: Assess today’s identity reality
- How NENS works with clients to prepare for Okta
- The roadmap: a phased rollout for efficacy, efficiency, and security
- NENS sample roadmap for a standard Okta implementation
- The ROI for SMB identity security
- In the meantime—spotting red flags
- Why Okta for SMBs—and how ZeroTek makes it practical
- Enterprise-grade protection for SMBs
Contents
- Why SMB identity security matters—and what IAM is
- The role IAM plays in protecting SMBs
- Getting started: Assess today’s identity reality
- How NENS works with clients to prepare for Okta
- The roadmap: a phased rollout for efficacy, efficiency, and security
- NENS sample roadmap for a standard Okta implementation
- The ROI for SMB identity security
- In the meantime—spotting red flags
- Why Okta for SMBs—and how ZeroTek makes it practical
- Enterprise-grade protection for SMBs
Key Takeaways
- SMB identity security is best anchored in Okta, using MFA, SSO, LCM, and Zero Trust to close the primary attack path.
- Structured implementation prioritizes consolidating and securing digital identities, then locking down email and productivity apps.
- Quantifiable ROI reduces incidents and yields significant productivity gains across users and IT.
- Trusted delivery: Proven IT service providers like NENS can bring a repeatable approach for a reliable, robust security.
Why SMB identity security matters—and what IAM is
If you run a small or mid-sized business (SMB), identity security can feel like “enterprise stuff.” It isn’t. Most successful cyberattacks start with compromised usernames and passwords, and SMBs see a disproportionate share of those attacks because they tend to have fewer controls in place. Identity and access management (IAM) coupled with a Zero Trust strategy tackles this risk head-on by controlling who can sign in to your apps and systems, how they prove it, and what they can touch once inside—every single time. The good news: modern IAM, powered by industry-leading Okta and delivered by your IT consultant or Managed Service Provider (MSP) through ZeroTek, gives you Okta’s enterprise-grade protection without enterprise-grade complexity or cost.
In this article, we’ll map how a typical Okta IAM rollout unfolds for SMBs—from the initial assessment and quick wins to a phased deployment, ROI, and red flags that warrant immediate action. Throughout, our co‑authors at New England Network Solutions (NENS) layer in real‑world perspective from delivering top‑tier identity security to SMBs.
This is the fifth of a weekly six-part series co-authored by ZeroTek and NENS for Cybersecurity Awareness Month (October). Some articles, like this one, are written for SMBs; others will address the concerns of MSPs.
The role IAM plays in protecting SMBs
The data is clear: it doesn’t matter if you’re a small shop with five staff or a global enterprise—if your business has digital identities, you’re a target. Today, most security incidents start with an account problem like stolen login credentials, a phished password, or a stale account still alive in three apps. IAM concentrates on this root cause.
With Okta as your identity layer, you get:
- Multifactor authentication (MFA) that’s resistant to phishing and supports biometrics (e.g., Face ID, fingerprint).
- Single Sign-On (SSO) that gives legitimate users frictionless access to what they need—without juggling passwords across apps.
- Automated Lifecycle Management (LCM) so staff changes (hires, role changes, departures) are handled correctly in seconds, not hours.
- Zero Trust: “never trust, always verify.” Every user, device, and request is continuously validated based on context (location, device posture, risk signals) to reduce your attack surface.
In short: if you’re asking “Do SMBs need IAM?”, the answer is yes—because identity is where attackers start, and it’s where you’ll get the biggest return on your security investment.
Getting started: Assess today’s identity reality
Your MSP or IT services provider will work with you to map:
- People: Who has access to what? There will be special focus on admins, executives, finance, HR, IT, and any contractors.
- Digital identities: Where do identities originate (HR, Microsoft 365/Entra ID, Google Workspace)? Are partners tracked?
- Systems: List apps by business criticality: email, file sharing, HR/payroll, accounting, CRM, industry-specific apps.
- Authentication: SSO or direct login? Is MFA enabled? Any legacy “basic auth” or app passwords?
- Provisioning: How do new hires get access—and how is access removed on departure? Manual steps = risk + cost.
- Devices and locations: Where do people sign in from? Which devices are trusted? This drives geofencing and device‑based controls.
Where Okta helps: centralized SSO, phishing-resistant MFA, policy controls, and lifecycle automation.
Why this matters: Okta + ZeroTek consolidates identities, enforces strong MFA, and automates joiner/mover/leaver workflows to remove human error and close gaps fast. Okta LCM automates provisioning/deprovisioning for 800+ apps and offers prebuilt SSO integrations for 8,000+ apps for rapid time‑to‑value (TTV).
“Our job is to make things simple, secure, and predictable for the client.”
– Jason Bricault,
CTO, NENS
How NENS works with clients to prepare for Okta
With over 60 SMBs and thousands of users on Okta, NENS follows a methodical, repeatable approach. “We start with a structured discovery to capture the client’s needs and expectations, including their business priorities, what apps they’re using, and their user experience goals. Once we have all the information we need, we sit down with leadership to review a clear plan: what we’re doing, why it matters, and when each step will take place,” explains Jason Bricault, CTO at NENS.
“Our job is to make things simple, secure, and predictable for the client,” says Bricault. “But they need to know what we’re doing and why. So we always preview the end-user experience and walk through essentials like the authentication factors we’re enabling for MFA, and take the time to confirm how the client’s security requirements will be enforced with Okta policies.”
The roadmap: a phased rollout for efficacy, efficiency, and security
Every successful IAM rollout follows a logical order: protect, automate, optimize. That’s why an MSP deploying Okta through ZeroTek will typically do it something like this:
Phase 1: Protect the most critical systems
- Consolidate all user identity directories and key platforms (Microsoft 365, Google Workspace, on-premises, or Azure AD/Entra ID) under Okta.
- Enforce phishing-resistant MFA and configure SSO for email, file storage, finance, HR/payroll, eliminating the use of passwords wherever possible for stronger identity security.
- Configure geofencing (allow from your normal regions; block known risky zones and Tor anonymizer proxies).
- Lock down admin access to Okta itself, and all apps with strong security policies.
- Turn on Okta ThreatInsight and basic protections against password-based attacks.
- Go live. Everyone starts using the Okta end-user dashboard for secure SSO access to all the apps they need.
Phase 2: Expand coverage and fine-tune automation.
- Bring remaining apps under Okta for SSO access through the end-user dashboard.
- Use LCM to automate onboarding/offboarding and group-based access so new hires have day-one access and departures lose access immediately.
Phase 3: Deepen Zero Trust strategy with device trust and FastPass.
- Require trusted devices for sensitive apps; apply risk‑based step‑up prompts when context changes (new location, unmanaged device, elevated privilege).
- Move toward passwordless with Okta FastPass.
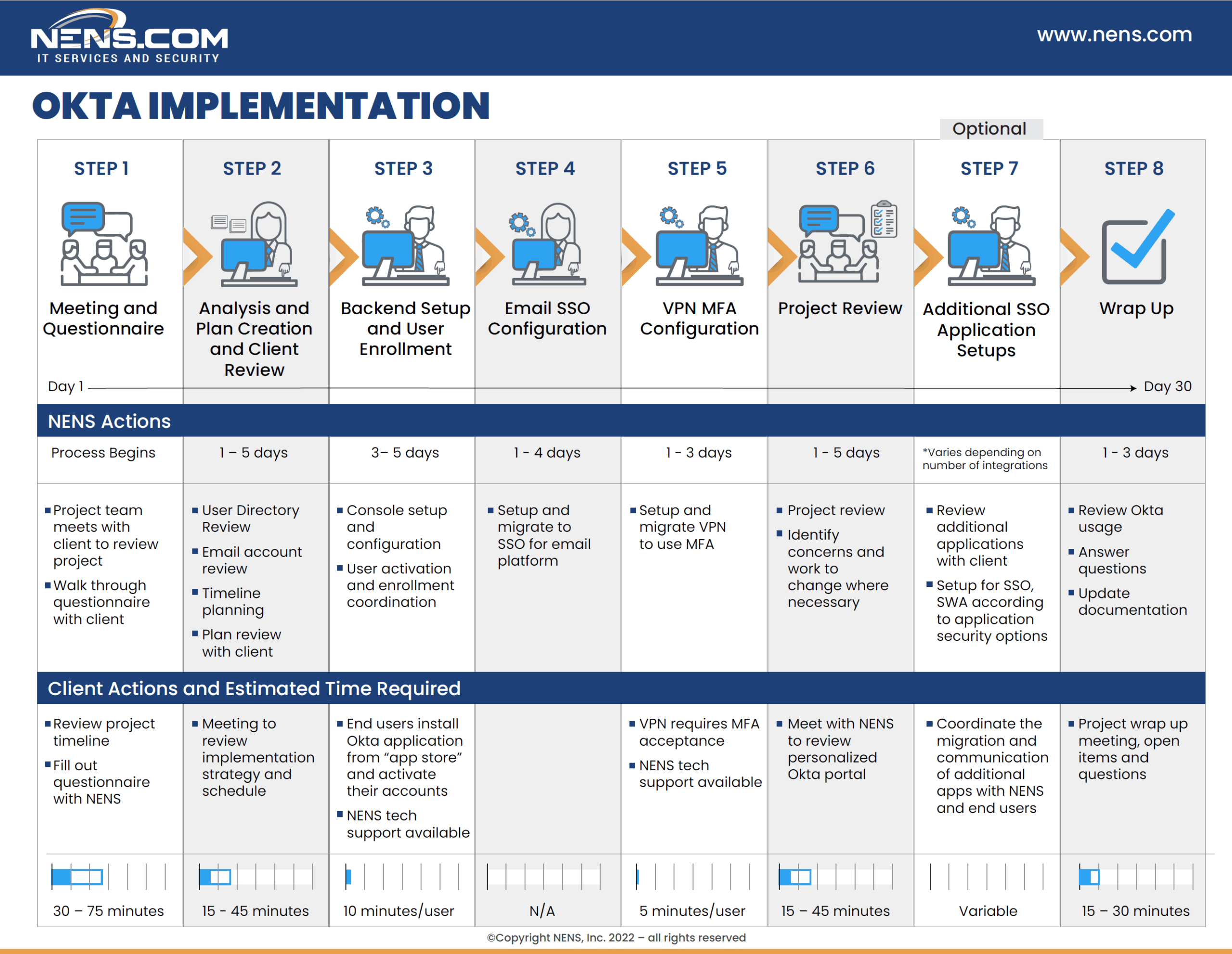
NENS sample roadmap for a standard Okta implementation
NENS standard roadmap for an Okta implementation is shown below, and covers Phases 1 and 2 listed above. NENS is also experienced in Phase 3 projects, which involve advancing a client’s Zero Trust strategy through device trust and streamlining passwordless access with Okta FastPass.
The ROI for SMB identity security
Assumptions (customize to your environment):
- Breaches avoided: Estimate the expected annual cost of identity-driven incidents you avoid (incident response, downtime, lost revenue, reputational harm). Even a single avoided incident can justify the project.
- IT time saved: Calculate hours saved by replacing manual account administration with automated provisioning/deprovisioning and group-based licensing. Multiply by fully loaded labor rates.
- End-user productivity: Factor in reclaimed minutes per user per day from SSO (fewer logins, no password resets, or password management).
- Licensing efficiency: With ZeroTek’s usage-based, monthly billing for Okta, you pay only for what you use—no big up-front commitments.
Back-of-the-napkin example:
- 100 employees, $50/hour blended rate.
- 10 minutes/day saved via SSO → ~40 hours/month → $2,000/month.
- 6 hours/month saved on provisioning and access changes → $300/month.
- Password reset tickets drop by 99% (assume 50/month at 10 minutes each) → ~8 hours → $400/month.
- Hard savings: ~$2,700/month before you count avoided incidents and insurance requirements.
For a 100-person business, that’s over $32,000 a year in recovered productivity before you even count the savings from avoided breaches.
In the meantime—spotting red flags
If you believe the old adage, “an ounce of prevention is worth a pound of cure” then it’s always a good time to improve your SMB’s identity security with Okta’s powerful IAM technology. But if you’re not working with an MSP or IT consultant yet, here’s a list of red flags that any non-technical person can look out for—any of them warrant attention.
Obvious signs you might be breached:
- Users keep getting locked out, or there are password reset prompts you didn’t initiate.
- Unexpected MFA-related emails. (For example: “Are you approving this sign-in?” spam).
- New admin accounts you didn’t create, or policy changes you didn’t approve.
- Successful logins from unusual countries.
Subtle signals worth investigating:
- Logins at odd hours for roles that normally work 9–5.
- Access attempts to payroll, HR, or finance apps from unmanaged devices.
- Inactive former employees still present in systems (especially shared admin or service accounts).
- A slow drip of password reset requests after a “phishy” email campaign.
When your MSP works with ZeroTek to give you Okta, they can block high-risk locations, create dynamic zones for your normal operating regions, and enforce step-up authentication or outright deny access when risk spikes. They can also use Okta ThreatInsight, which adds another layer that logs and enforces protection based on known malicious behavior. Moving away from passwords to passwordless authentication eliminates significant vulnerabilities, as does introducing device-based security—all easy to do with Okta.
CASE STUDY: Read how NENS stopped an attack and secured a customer with a same-day Okta deployment.
Why Okta for SMBs—and how ZeroTek makes it practical
“Can a small business use Okta?” Yes—through an MSP or IT consultant that partners with ZeroTek. Okta is a leading IAM platform with deep SSO integrations and advanced MFA options, while ZeroTek gives your MSP the multi-tenant controls, role-based auditing, and consumption-based licensing SMBs need. Your MSP can spin up a new Okta tenant in minutes, manage all customers from a single pane of glass, tightly control who on their tech team has access, and standardize security while fine-tuning configurations for each client. That translates to faster deployment and stronger outcomes for you.
“Do SMBs need IAM?” If you use cloud apps, store customer data, handle payroll, process payments, or support remote work, the answer is yes. IAM isn’t a “nice to have”; it’s the control layer that makes Zero Trust security doable for small teams.
“What’s the best IAM for SMBs?” The “best” choice balances security with usability and cost. Okta’s breadth of app integrations and modern authenticators checks the security box; ZeroTek’s MSP-grade multitenancy, auditability, and monthly per-use licensing checks the practicality box. Together, they deliver enterprise-grade identity protection for SMBs.
Enterprise-grade protection for SMBs
You don’t have to spend like a large enterprise to protect identities like one. SMBs like yours are targeted every day; but strong MFA, SSO, and lifecycle automation stop most attacks before they start. Partnering with your MSP, Okta and ZeroTek makes these safeguards quick to adopt and easy to run—so you harden defenses, speed onboarding and offboarding, and eliminate password chaos all at once.
NENS x ZeroTek
New England Network Solutions (NENS) brings deep frontline MSP expertise, while ZeroTek’s multi-tenant Okta control plane makes it easy to standardize and scale best-practice identity security for SMBs. With ZeroTek | Okta, NENS rolls out strong, consistent controls quickly, cuts risk without adding complexity and delivers enterprise-grade protection to all customers.
Are you ready?
Ready for an easier way to deliver strong identity security and audit success to your SMB clients?

MSPs and IT service providers: book a 1:1 consultation to discover how you can deliver excellence with ZeroTek | Okta.




